Infrastructure Security
Every node on your network presents an attack surface for skilled cybercriminals. A penetration test targeted at your infrastructure helps reveal those vulnerabilities before they can be exploited.
Every node on your network presents an attack surface for skilled cybercriminals. A penetration test targeted at your infrastructure helps reveal those vulnerabilities before they can be exploited.






Weaknesses within your network infrastructure are used by cyberattackers to gain entry to protected resources – like personal data or financial systems. Once inside your network, attackers can exfiltrate data, extort money or cause general disruption and destruction.
An infrastructure assessment probes your network nodes and software, identifying vulnerabilities before they are exploited. Using the same tools and techniques as the criminals, Wavenet consultants scan and analyse every aspect of your infrastructure searching for weaknesses that need to be addressed.


Prioritised action
plan An infrastructure assessment will identify and prioritise vulnerabilities. The test results report includes an action plan so you know what to address first.
Check your security provisions
Your network will already include a number of security provisions – but are they still effective? An infrastructure assessment will confirm their effectiveness and advise on potential improvements that could be made.
Routine system testing
Some frameworks, like PCI DSS, demand regular testing of security provisions. Infrastructure assessment services from Wavenet will ensure you meet your compliance requirements and achieve the necessary certifications.
Protect your customers
Customers are increasingly concerned about how their personal data is treated by businesses. Infrastructure tests prove that you are taking customer privacy seriously.
Secure your corporate reputation
As well as fines and costs associated with network infrastructure breaches, your corporate reputation will also suffer. Fixing problems before they are exploited will keep customers on board – and help to attract new ones too.
Wavenet consultants start every infrastructure assessment from the assumption that your network has already been breached. We search for potential weaknesses at the node level and the tell-tale signs that they have already been exploited.
Every application represents a potential attack surface. The Wavenet team will audit all of your software assets, paying special attention to those applications which are out of date, or unsupported by the vendor. We can help you draw up an action plan for applying the necessary patches and bringing applications up to date.
Every infrastructure assessment looks at passwords, protocols and permissions for servers, systems, applications and file stores. We help you identify misconfigurations, default credentials and improperly secured files that provide easy access for criminals.
To reduce the chance of risk factors being missed, Wavenet combine automated vulnerability scanning tools with the knowledge and experience of their consultants. This is exactly the same approach adopted by cybercriminals, giving Wavenet infrastructure assessments – and results – increased credibility.
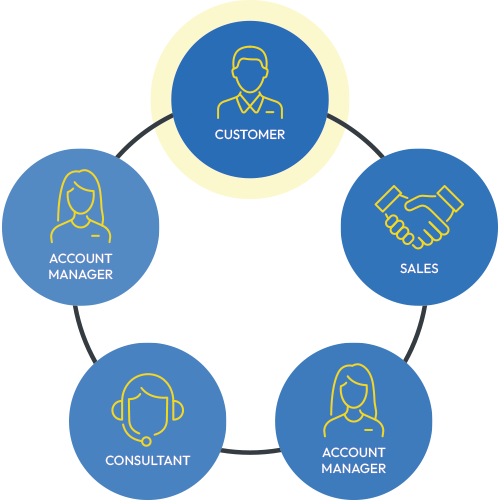
Other approaches we've witnessed have included convoluted steps and commonly ends with incorrect information being handed to the consultant assigned to the engagement.
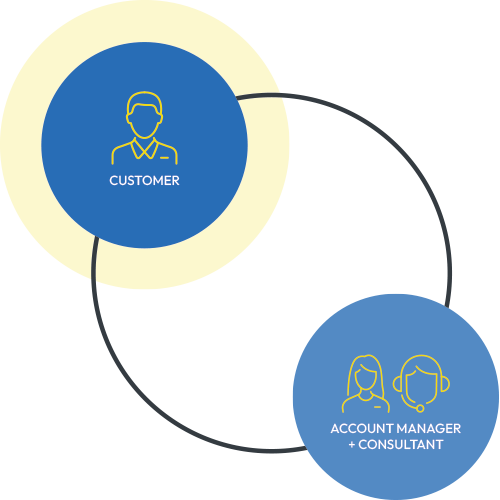 Our approach to security involves a qualified security consultant through the entire process to ensure quality, accuracy and consistency.
Our approach to security involves a qualified security consultant through the entire process to ensure quality, accuracy and consistency.



Oysta is very happy with the support, service and dedication of the Wavenet team. Working with the Oysta team every step of the way, not only did they check all security on the device, they also provided feedback on the quality of the hardware. I will be working with Wavenet again.
Mario Zuccaro, Founder and CEO, Oysta TechnologyWe have been really pleased with the service provided by Wavenet. We have found them to be extremely easy to work with. We also felt their fee structure was reasonable. We would recommend Wavenet to anyone looking for a PCI pen testing partner.
Andy Phillips, Inspired OutsourcingGreat service. Gave us exactly what we needed, as promised.
Philip Cunnington, TalkPlus NHSWe were extremely pleased with the service, knowledge and professionalism shown by Wavenet. After the remediation phase, we then ran a phishing exercise with them to remind staff of the need to be vigilant with external email communications. I would have no hesitation in using or recommending Wavenet in the future due to the quality of work carried out at a great price.
Graeme Thistlethwaite, ICT, Business Change and Business Support ManagerWavenet provided a high quality penetration service at a reasonable price … communications were great … the Pen test team flexed around us and our other commitments to get the job done. Thanks!
Darren Crombie, CEO, Upstream OutcomesGet all the latest news and insights straight to your inbox.
Just submit your details and we’ll be in touch shortly.