Red Team Assessment
The only way to truly assess your IT security is to experience a cyberattack. Our Red Team Assessment uses real hacking tools and techniques to test your systems.
The only way to truly assess your IT security is to experience a cyberattack. Our Red Team Assessment uses real hacking tools and techniques to test your systems.






Using the same tools and techniques employed by hackers, a Red Team Assessment looks and feels like a real cyberattack. The idea is to test your defences against attack, and your response to a security incident.
The only difference is that all testing is carried out by ethically-trained cybersecurity professionals. There is no lasting damage to your systems, and data is never exposed to third parties. But you do find out exactly where your network defences need additional work and target investment accurately.


Real hacking insights
Under test conditions, you can get a reasonable idea of how well your defences perform. But a Red Team Assessment places those defences under real stress – just like a hacker would. This is the only way to see whether your business is truly protected.
Assess people and technology
Effective security is a mix of people, processes and technology. Hackers focus on all three to gain access to your network, so an effective test must go beyond just technical considerations.
Analyse your security response
How your business reacts to a successful breach is just as important as your efforts to keep hackers out in the first place. A Red Team Assessment can help you identify strengths and weaknesses, and fine tune your processes for future events.
Test your latest investments
When deploying new security measures, the best way to confirm correct installation and configuration is by testing it. And what better test than placing new software and systems under the strain of a real-world simulation?
Identify shortfalls
A successful network breach by the Red Team will expose vulnerabilities in your people, processes and technology. You will identify opportunities for new, targeted investment, or issues that require additional staff training.
Our Red Team will attack people, processes and technology simultaneously using automated tools, experience and social engineering techniques. By testing everything, you get a full 360º view of your security provisions.
When a hacker cannot gain access remotely, they will sometimes try to gain physical access to your systems. Our Red Team makes anonymous site visits to check your physical security provisions – and the awareness of your employees.
Infected email attachments remain an effective way to compromise defences – so we mimic the technique. Our phishing tests verify the effectiveness of your anti-malware systems. We also check staff responses to receiving phishing emails, identifying knowledge and skills shortfalls.
Echoing the step-by-step approach used by advanced persistent threat (APT) groups, our consultants will attempt to compromise a range of network nodes. We will then demonstrate data theft, logon account compromises and the potential for infrastructure damage.
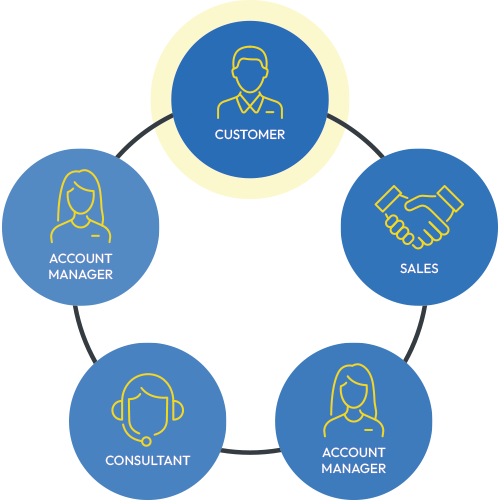
Other approaches we've witnessed have included convoluted steps and commonly ends with incorrect information being handed to the consultant assigned to the engagement.
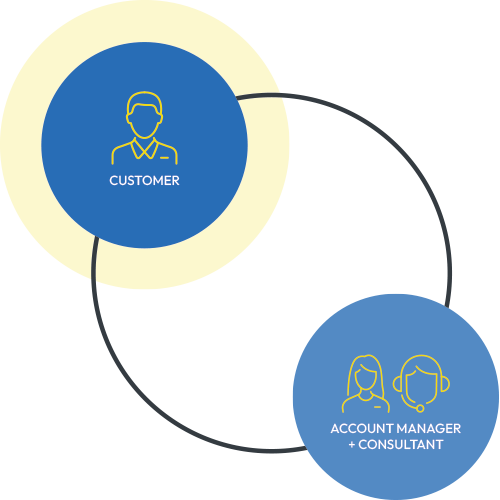 Our approach to security involves a qualified security consultant through the entire process to ensure quality, accuracy and consistency.
Our approach to security involves a qualified security consultant through the entire process to ensure quality, accuracy and consistency.



Oysta is very happy with the support, service and dedication of the Wavenet team. Working with the Oysta team every step of the way, not only did they check all security on the device, they also provided feedback on the quality of the hardware. I will be working with Wavenet again.
Mario Zuccaro, Founder and CEO, Oysta TechnologyWe have been really pleased with the service provided by Wavenet. We have found them to be extremely easy to work with. We also felt their fee structure was reasonable. We would recommend Wavenet to anyone looking for a PCI pen testing partner.
Andy Phillips, Inspired OutsourcingGreat service. Gave us exactly what we needed, as promised.
Philip Cunnington, TalkPlus NHSWe were extremely pleased with the service, knowledge and professionalism shown by Wavenet. After the remediation phase, we then ran a phishing exercise with them to remind staff of the need to be vigilant with external email communications. I would have no hesitation in using or recommending Wavenet in the future due to the quality of work carried out at a great price.
Graeme Thistlethwaite, ICT, Business Change and Business Support ManagerWavenet provided a high quality penetration service at a reasonable price … communications were great … the Pen test team flexed around us and our other commitments to get the job done. Thanks!
Darren Crombie, CEO, Upstream OutcomesGet all the latest news and insights straight to your inbox.
Just submit your details and we’ll be in touch shortly.