Stolen Device Assessment
How much damage could a lost smartphone do? The Stolen Device Assessment will help you know for sure.
How much damage could a lost smartphone do? The Stolen Device Assessment will help you know for sure.






Indispensable in the mobile workplace, smartphones, tablets and laptops allow your employees to be productive any place, any time. But if one of these devices is stolen, hackers have direct access to some of your most sensitive systems and data.
The Stolen Device Assessment will help you understand those risks, and how prepared you are to deal with them. Our consultants will simulate a cyberattack using a ‘stolen’ device, analysing the performance of your defences and processes in dealing with this all-too-common occurrence.


A stolen device is a security backdoor
Stolen devices make it simple for hackers to gain access to secure resources because the system is already trusted. Many use cached credentials to log in to the corporate network, giving attackers an instant foothold and reducing the time and effort required to break in.
Devices store data
Mobile devices typically store data locally, some of which may contain sensitive details. Stealing a device may provide hackers with access to valuable IP or expose personally identifiable information (PII) in breach of the GDPR.
Assess encryption and sandboxing provisions
Measures like disk encryption and app sandboxing can secure locally-stored data – if it has been deployed and maintained correctly. A stolen device assessment will investigate the efficacy of your data security measures.
Initial tests will focus on breaking into the stolen device itself. Our consultants will try to extract PII and other sensitive data directly from the local storage.
Cached credentials and passwords provide authorised access to your network. We will attempt recovery of these details from a ‘stolen’ device.
Using a ‘stolen’ device, our engineers will breach your network. Penetration testing allows you to assess how effective security provisions, and which data stores and applications are most at risk.
As well as exposing vulnerabilities in your existing mobile environment, our report will help you plan for the future. Our consultants will also help you plan the necessary safeguards to protect your network as it evolves and develops in future.
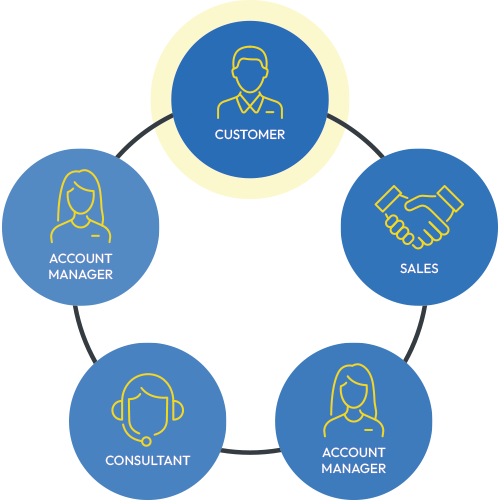
Other approaches we've witnessed have included convoluted steps and commonly ends with incorrect information being handed to the consultant assigned to the engagement.
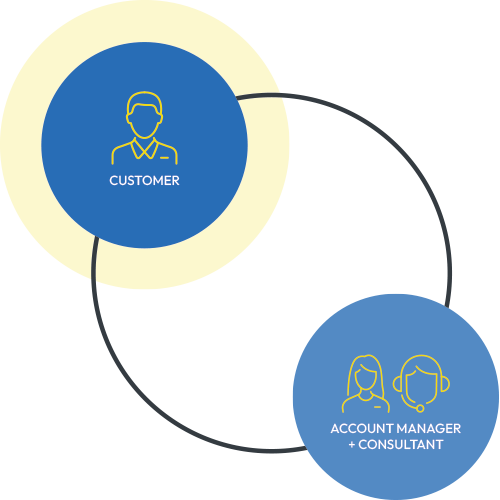 Our approach to security involves a qualified security consultant through the entire process to ensure quality, accuracy and consistency.
Our approach to security involves a qualified security consultant through the entire process to ensure quality, accuracy and consistency.



Oysta is very happy with the support, service and dedication of the Wavenet team. Working with the Oysta team every step of the way, not only did they check all security on the device, they also provided feedback on the quality of the hardware. I will be working with Wavenet again.
Mario Zuccaro, Founder and CEO, Oysta TechnologyWe have been really pleased with the service provided by Wavenet. We have found them to be extremely easy to work with. We also felt their fee structure was reasonable. We would recommend Wavenet to anyone looking for a PCI pen testing partner.
Andy Phillips, Inspired OutsourcingGreat service. Gave us exactly what we needed, as promised.
Philip Cunnington, TalkPlus NHSWe were extremely pleased with the service, knowledge and professionalism shown by Wavenet. After the remediation phase, we then ran a phishing exercise with them to remind staff of the need to be vigilant with external email communications. I would have no hesitation in using or recommending Wavenet in the future due to the quality of work carried out at a great price.
Graeme Thistlethwaite, ICT, Business Change and Business Support ManagerWavenet provided a high quality penetration service at a reasonable price … communications were great … the Pen test team flexed around us and our other commitments to get the job done. Thanks!
Darren Crombie, CEO, Upstream OutcomesGet all the latest news and insights straight to your inbox.
Just submit your details and we’ll be in touch shortly.